A redhead instant messaged me. She was in a vacation home on the Massachusetts coast. "Fleishman," she typed breathily. "You're the only one with the answer." "Spill the Java applets, toots," I tapped out with one hand while knocking back ban-cha tea with the other. A pause. Then a stream of words. "My Android phone won't connect to my MacBook Pro's software base station. My husband doesn't understand. I need your help." I like a challenge. I rolled up my hemp-cotton sleeves. "Lady, I charge 128 bits a day, plus expenses." She agreed.
I had a mystery to unravel: why couldn't her Android phone connect to a feature that's been in Mac OS X for years, and which she'd used successfully before with other devices? What was unique about either the phone or the setup? And could I work through the technical answer in the style of 1930s pulp-fiction detective?
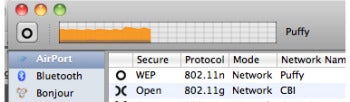 The mystery started with a Mac OS X software base station that was talking out of both sides of its mouth: 802.11n and WEP aren’t compatible. What gives?
The mystery started with a Mac OS X software base station that was talking out of both sides of its mouth: 802.11n and WEP aren’t compatible. What gives?I checked out her problem. It seemed legit enough. She set up password-protected access to her Mac over Wi-Fi. The moll typed in the same password into her Android phone. No dice. After turning encryption off on the Mac, the Page-and-Brin bruiser from Mountain View managed to hook up just fine. Neat. But too neat. What were Sergei and Larry up to? Could this Wi-Fi shamus sort it out?
If you want the inside skinny without a cherry on top, skip to the end, where I spell it out in black and white.
The Apple Side
Apple's software base station makes its home in the Sharing system preference pane in the Internet Sharing service. The notion--and apparently some of the code--dates back more than a decade to when this feature was first added to Mac OS 8. The feature disappeared in Mac OS X, but was restored due to popular demand.
Software base station is showing its age. Even though Macs have shipped for years with both 2.4 GHz and 5 GHz Wi-Fi available, Internet Sharing only uses the weak-kneed 2.4 GHz band, prone to congestion and interference. (Also, a mean drunk. Never get into a fight at 2.4 billion cycles a second after insulting WEP's robustness in a crowded RF environment.)
And worst of all, the software base station offers only WEP (Wired Equivalent Privacy) encryption, a broken standard that's been beaten so many times that there's hardly a bone in its protocol body that's not shattered. WEP isn't just a last resort for encryption--it's the worst resort. A kid with an Asus netbook could download free software and be through your WEP defenses in a few minutes. Child's play.
Still, I knew that Internet Sharing over Wi-Fi worked. I'd used it myself plenty of times on the road, when paying for a hotel connection over Ethernet, and sharing via Wi-Fi on my laptop to access the Internet from other devices. (The reverse works, too: a Wi-Fi connection can be shared via Ethernet, or even Bluetooth.)
I started wearing out some shoe leather sorting out the problem. My first lead came from sniffing the air. The software base station on a newer Mac, one with 802.11n networking built in, offers up an incompatible set of standards when WEP is turned on. 802.11n defines its only encryption type as WPA2 (Wi-Fi Protected Access's second version), which dates to 2004. (Technically, it requires the AES-CCMP encryption key type, but don't let me flap my jaw at you about details.)
That seemed like it might be the culprit. But after more investigation, the trail went cold: properly functioning Wi-Fi clients will back off on the gas, and use the slower 802.11g standard to connect over WEP. Android was innocent, and I didn't have a second suspect.
A Dead End?
I'd hit a dead end in the case. Sitting with my feet up on my desk in a smoky office lit in chiaroscuro, I remembered: reading! Words mean things! I could read, and read I did. Returning to the Internet Sharing service in Mac OS X, I found these words I'd skipped before:
"If you plan to share your Internet connection with non-Apple computers, use a 5 character password for a 40-bit WEP key, and a 13 character password for a 128-bit WEP key."
Of course! The room became even hazier as flashback lines rippled in my field of vision. It was all coming back to me. The year was 1999. I was young then, and in love with Wi-Fi--and WEP. That was before everything went wrong.
Back then, when 802.11b was introduced and Wi-Fi made itself known to the world, WEP was considered an acceptable compromise to secure the traffic between a Wi-Fi adapter on a laptop, like toilet-seat iBooks, and a Wi-Fi router, such as Apple's AirPort Base Station. You had to throw down 30 sawbucks ($300) for a device that seems today as slow as a Model T Ford in a NASCAR race. But then it was a miracle, and every day was sunny. I was in love. Remember?
Apple tries to be everyone's buddy, so they made it nice and easy to bypass a real irritation with WEP. Seems that WEP was particular--too particular, most people say. With the first version, 40-bit WEP (referring to the length of the encryption key), you had to come up with five letters and numbers (A-Z, a-z, and 0-9), or ten digits in base 16 (hexadecimal), from 0 to 9 and A to F; A to F correspond to 10 to 15. A later so-called improvement--which turned out to be window dressing--used 128-bit keys, which required 13 letters and numbers or 26 hex digits.
Most normal people had a problem with that. "Too much palaver," I'd hear in dingy Internet cafés. Apple has moxie. The Cupertino capybara figured out a way to make WEP simpler. That's Apple's M.O. The engineers came up with a method to turn a series of text into a WEP key without requiring users to come up with something that fit into the straitjacket of WEP's built-in limits. That came with a price--a price that my flamehaired friend was paying today as my flashback ended.
You see, Apple let you create a key with any AirPort system and the software base station of any length, working its mumbo-jumbo behind the scenes to create a perfect WEP key. It always makes a WEP key of the right length and type no matter what you type, but type the correct length and you get an exact match.
We've forgotten all that horror since WEP was superseded by WPA in 2003 and WPA2 a couple of years later. WPA and WPA2 let you enter a bunch of plain text and punctuation, for a total ranging from 8 to 63 characters. The WPA and WPA2 algorithm transforms those characters into the underlying encryption key no matter what computer, mobile phone, E-Z-bake-oven-with-remote-Wi-Fi controls, or game system you use. WEP lost my heart when WPA2 gained it. You never forget your first love, no matter how flawed, even when you've outgrown it.
How I Cracked the Case
I hoofed it to 1 Infinite Loop for some answers. After driving around endlessly, I ditched the motor. I knocked on a banged-up door marked PR. "Beat it," a gravely voice muttered through a crack. "It's Fleishman. It's about the software base station. You know. That thing you want to pretend is a feature. But that doesn't get updated." "Take a hike, detective," the voice replied, as I pushed my Pringles can antenna into the gap. I said, "I just want to know: do Androids dream of encrypted WEP?" "I can't say much," came the reply. "But try 5 and 13 letters. No more. No less." The Pringles can dislodged, and the door slammed. I had my tip.
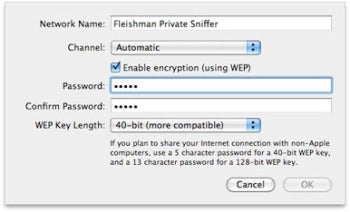
Returning to my office, I tapped the keyboard to wake the machine, fired up Internet Sharing, clicked the AirPort Options button, made sure 40-bit WEP was selected in the WEP Key Length popup, and pecked out:
redhd
I clicked OK. I selected Ethernet (my Internet source) from the Share Your Connection From menu, and then checked the AirPort box in the To Computers Using list. I then clicked the checkbox next to Internet Sharing to start up the engine.
With an Android phone that conveniently fell off a truck, I used the Settings app to bring up a list of Wi-Fi networks, selected mine, and tapped away:
redhd
 I cracked my fingers and entered redhd into the WEP password fields, a five-letter password that was my key to breaking this case wide open.As I watched gears click into place, I knew I had a winner. The phone connected, got an IP address, and started purring along. But I wasn't hearing gears click--no, it was the sound of an instant message alert. I fired up video and saw a smartphone pointed right at my temples.
I cracked my fingers and entered redhd into the WEP password fields, a five-letter password that was my key to breaking this case wide open.As I watched gears click into place, I knew I had a winner. The phone connected, got an IP address, and started purring along. But I wasn't hearing gears click--no, it was the sound of an instant message alert. I fired up video and saw a smartphone pointed right at my temples."So, shamus." It was my crimson colleague. "You figured it out."
"Back off, doll, I've got the ticket right here." She lowered the phone, and I explained the situation. She set up her machine, punched in a five-letter password, and connected from her Android. "It works," she said. "You are going to get massive rock star status for this one, Fleishman."
I explained to her that it also works with the original AirPort Base Station, which can only run WEP, and with WEP enabled on newer (2003 and later) base stations set to use that standard. While I was used to the AirPort Base Stations pushing up daisies through a power-supply failure a few years into operation, my friend still could "see" two across the street from her office. "We're a public college, Fleishman. We use what we have."
And if the 5- or 13-character ASCII password trick didn't work, I had another tip. In the software base station in Mac OS X, you can force the use of hexadecimal by using a dollar sign--thank you, Uncle Sam--in front of a series of 10 or 26 hex digits for 40- or 128-bit WEP. For instance:
$A0B1C2D3E4
On an Android phone, under Windows, or elsewhere, you type that sequence in omitting the dollar sign as:
A0B1C2D3E4
"You think you're pretty clever, dick," my friend said. "But what do you think of--this!" A Star.me invite. Oh my stars, indeed. I may have started out illiterately staring down the wrong end of a telescope, and ending up seeing stars, but the case was closed. Time for a night cap of ginger and seltzer.
The Plain Truth
The problem my friend Kerri encountered and I figured out with her help, some advice from Apple engineers, and, as I note above, reading Apple's text more carefully was a mismatch between what you are may set as a password for the Internet Sharing service's WEP encryption key, and what works compatibly with Apple and non-AirPort gear.
Here's how to set this up so you can get a reliable connection with Android and other mobile devices, Windows systems, and Linux and beyond, as well as Mac OS X and iOS devices. (This also works with the original AirPort Base Station via the AirPort Admin Utility, and with later base stations set to 802.11g and WEP in AirPort Utility in the places in the utility that let you set a password.)
Now on another device, such as an Android phone, select your Mac's software base station by name. You should be prompted to enter a WEP password. If given an option among types (like hex and ASCII), choose ASCII. Enter the password precisely as you set it on the Mac.
You should now be connected.


 18:07
18:07
 Hassaan Syed
Hassaan Syed


 Posted in:
Posted in: 


1 comments:
pusulabet
sex hattı
https://izmirkizlari.com
rulet siteleri
rexbet
63BY0T
Post a Comment